Smart Buildings and Enhanced Security Features
Contemporary security solutions for buildings have undergone remarkable transformations, introducing sophisticated methods for safeguarding both physical assets and digital information. These integrated systems utilize state-of-the-art innovations including machine learning, Internet-connected devices, and distributed computing to establish comprehensive protective measures. This thorough analysis will explore the fundamental elements and advantages of today's building security technologies.
The harmonious combination of multiple technological platforms creates an adaptive and responsive security infrastructure. This infrastructure can identify and react to potential security incidents as they occur, substantially reducing exposure to threats while maintaining a protected space for all building users. Remote monitoring and administration of security protocols represents a significant benefit that conventional systems frequently cannot match.
Essential Elements of Contemporary Building Security
Modern building protection systems typically incorporate interconnected networks of detection devices, surveillance equipment, and entry management solutions. These components collaborate to deliver comprehensive security coverage. For instance, motion sensors can initiate alerts when detecting abnormal movement patterns, while integrated camera systems enable live observation of potentially concerning scenarios.
Sophisticated analytical capabilities, frequently enhanced by machine learning algorithms, play an increasingly vital role. These systems can process information from multiple sources to recognize behavioral patterns and irregularities, facilitating preemptive threat identification and resolution. This forward-thinking methodology proves indispensable when addressing today's complex security challenges.
Advantages of Modern Security Implementations
Deploying advanced security systems provides numerous benefits, including heightened protection and minimized vulnerabilities. These solutions offer superior security by detecting and addressing potential threats more rapidly than conventional alternatives. This accelerated reaction capability often proves critical in preventing or reducing the consequences of security incidents.
Enhanced operational effectiveness represents another notable advantage. Automated processes and continuous monitoring enable security teams to concentrate on more complex responsibilities, improving personnel deployment and decreasing intervention times. These optimizations result in greater overall efficiency and long-term financial benefits.
Emerging Directions in Building Security Technology
The trajectory of building security technology points toward continuous innovation and system integration. Anticipate more sophisticated machine learning-powered threat identification and response mechanisms, along with tighter coordination with other facility management solutions. This synergy will facilitate a more unified strategy for building administration and protection.
The growing adoption of biometric verification and other advanced authentication techniques will further strengthen security protocols. This ongoing progression ensures that intelligent structures maintain their position at the vanguard of security innovation.
Advanced Surveillance Systems: From Traditional to AI-Powered
Modern Surveillance Capabilities
Cutting-edge monitoring systems are revolutionizing environmental observation and protection approaches. These solutions extend beyond simple visual recording, integrating advanced technologies to produce detailed and practical insights. These enhanced capabilities permit more thorough event analysis, resulting in faster responses and superior protective measures. Complex algorithms and pattern recognition technologies enable the identification of trends and deviations, allowing preventative actions before situations intensify.
Diverse monitoring technologies, including thermal detection and sound analysis, supplement visual recording to provide complete environmental awareness. This multi-faceted approach dramatically improves data accuracy and reliability, delivering comprehensive situational understanding. The synthesis of multiple data streams creates a robust and complete monitoring framework.
Practical Applications of Advanced Monitoring
State-of-the-art surveillance systems boast extensive applications beyond basic security functions. From infrastructure oversight and public area monitoring to critical facility protection and safety compliance enforcement, the potential uses are vast. This encompasses traffic pattern analysis, environmental risk detection, and even potential threat forecasting based on historical data trends. Timely identification of irregularities is essential for successful intervention and risk management.
Within industrial environments, these systems can track equipment performance, anticipate possible failures, and enhance production efficiency. This preventative strategy reduces operational interruptions and maximizes output. Advanced analytics can also pinpoint process improvement opportunities, leading to significant cost reductions.
Technological Foundations of Modern Surveillance
Advanced monitoring systems employ an intricate combination of technologies to achieve their sophisticated functionality. These include high-definition cameras, complex image analysis algorithms, and advanced data storage solutions. Live video transmission and automatic notification systems represent critical elements of these configurations. This sophisticated technological integration enables rapid identification and reaction to potential threats and incidents.
Additionally, these systems utilize pioneering technologies like artificial intelligence and machine learning to analyze data and detect patterns invisible to human observers. The application of AI and ML is essential for automating processes and facilitating immediate decision-making. This substantially improves surveillance system performance and effectiveness.
Future Development of Monitoring Technologies
The evolution of surveillance systems will feature increasing sophistication and integration with complementary technologies. Expect expanded utilization of networked devices for environmental data collection, and the consolidation of information from various sources to create more complete situational awareness. This integration will facilitate more proactive and adaptable systems. Development of more intuitive interfaces and sophisticated analysis tools will also represent key trends.
The convergence of multiple technologies, including artificial intelligence, large-scale data analysis, and cloud-based computing, is driving surveillance system evolution toward more intelligent and proactive solutions. This will lead to even greater efficiency and effectiveness in observing and safeguarding various environments.

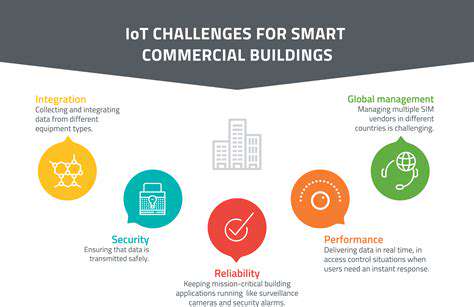
IoT Integration and Data Security: A Holistic Approach
Implementing Strong Data Protection for Connected Devices
A fundamental aspect of securing IoT implementation in modern buildings involves deploying robust data encryption methods. Encryption guarantees that confidential information transmitted between devices and central systems remains protected, preventing unauthorized access. Techniques like AES (Advanced Encryption Standard) and TLS (Transport Layer Security) are commonly used to secure stored and transmitted data respectively. By implementing comprehensive encryption protocols, facility management systems can preserve the integrity and confidentiality of occupant information, operational data, and security notifications.
Furthermore, the continuous advancement of encryption standards requires regular updates and security patches for networked devices. Obsolete or weak encryption methods can become vulnerable over time, potentially compromising the entire building infrastructure. Consequently, incorporating automated security measures that adapt to emerging threats is crucial for maintaining strong protection. Facility administrators should also consider deploying dedicated security hardware that provides additional encryption management, ensuring secure key storage and tamper-resistant operations.
Establishing Multi-Layered Verification and Permission Systems
In the context of intelligent buildings, controlling access to connected systems is vital to prevent unauthorized modification of building functions like lighting, climate control, and security cameras. Multi-step verification enhances security by requiring users to confirm their identity through multiple methods, such as passwords, biometric verification, or physical tokens. This approach substantially decreases the risk of credential compromise and unauthorized access, particularly for system administrators handling sensitive configurations.
Complementing multi-step verification, implementing strict permission policies ensures users only have access appropriate to their responsibilities. Responsibility-based access systems can limit device and data access according to predefined user roles, reducing the possibility of accidental or intentional misuse. Routine audits and real-time monitoring of access records are essential for promptly identifying and addressing suspicious activities, thereby maintaining the security integrity of the building's connected ecosystem.
Protecting Network Infrastructure for Connected Devices
Modern buildings depend heavily on interconnected networks to facilitate seamless data exchange between devices. Securing this network infrastructure requires implementing protective barriers, intrusion detection mechanisms, and secure communication channels to establish a fortified perimeter around connected devices. Dividing the network into isolated segments can contain potential breaches, preventing malicious software or intruders from spreading throughout the entire facility management system.
Additionally, conducting regular network security evaluations and vulnerability scans can identify weak points before they are exploited. Network administrators should enforce strict credential policies and disable unnecessary functions on connected devices to minimize potential attack vectors. Ensuring that all network-connected devices have current firmware and software is essential for addressing known vulnerabilities and maintaining overall security resilience.
Developing Comprehensive Security Strategies for Connected Systems
A thorough security approach for IoT implementation in modern buildings requires a holistic perspective incorporating hardware, software, policies, and user practices. Establishing clear security standards during the design phase ensures protection is incorporated at every system level. Cooperation between device manufacturers, system integrators, and facility operators is necessary to align security practices with industry standards and regulatory requirements.
Educating staff and occupants about security awareness can significantly reduce risks associated with human error, such as falling for fraudulent schemes or mishandling access credentials. Regular security assessments, incident response planning, and continuous monitoring provide the necessary structure to quickly detect, respond to, and recover from security events. Ultimately, integrating security considerations into the foundation of connected system deployment enables the creation of more intelligent, safer buildings capable of adapting to changing cybersecurity environments.
Harmonizing Innovation with Security in Building IoT Systems
While implementing innovative connected solutions can dramatically improve building efficiency and occupant comfort, it also introduces new security challenges that must be carefully addressed. Emerging technologies like AI-driven automation, decentralized computing, and predictive analysis offer powerful capabilities, but they also expand potential vulnerabilities if not properly secured. Building operators need to assess the security implications of adopting new technologies and implement appropriate safeguards.
Cultivating a security-focused mindset promotes continuous evaluation and proactive mitigation of risks associated with technological progress. This includes maintaining adaptable security architecture capable of accommodating new devices and protocols, as well as establishing partnerships with cybersecurity specialists. By achieving equilibrium between embracing innovation and enforcing rigorous security measures, modern buildings can realize their full potential without compromising safety or data protection.