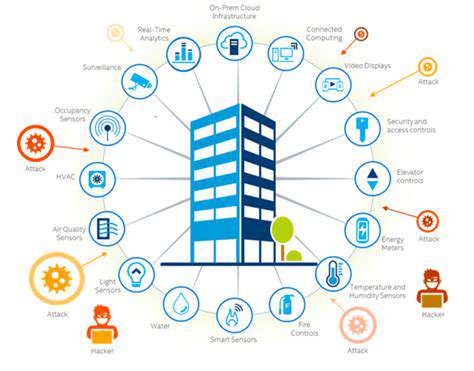
Smart Buildings and Enhanced Cybersecurity Measures

Proactive Security Measures for Smart Building Systems
Proactive Prevention Strategies
Forward-thinking security approaches have become indispensable for shielding systems and sensitive information from emerging dangers. These methodologies emphasize identifying and neutralizing risks before they escalate into major incidents. Deploying stringent protective measures—such as complex passphrases, layered verification processes, and consistent system patches—forms the foundation of defense against unauthorized intrusions and malicious software. Organizations that prioritize vulnerability management dramatically lower their exposure to potential breaches.
Comprehensive education programs for staff members represent another critical preventive measure. These initiatives arm employees with practical skills to recognize and escalate questionable behaviors, deceptive email attempts, and other security red flags. An informed team serves as the most effective barrier against digital intrusions. This knowledge-sharing fosters an environment where security consciousness becomes second nature, transforming personnel into vigilant guardians of corporate digital resources.
Implementing Advanced Security Tools
The integration of sophisticated protective technologies—including network monitoring systems, digital barriers, and device security solutions—has become non-negotiable for early threat detection. These solutions offer continuous surveillance and evaluation of data flows, enabling the identification of suspicious patterns before they impact critical infrastructure. Proactive deployment of such technologies positions enterprises to anticipate emerging risks and sustain formidable defenses.
Systematic security evaluations and controlled vulnerability assessments form equally vital components of an anticipatory protection strategy. These examinations reveal weak points in technological frameworks, permitting organizations to reinforce potential entry points. Continuous vulnerability remediation constitutes the cornerstone of effective digital protection. Simulated cyberattacks provide realistic performance metrics for security protocols, pinpointing areas requiring enhancement and directing corrective actions.
Developing a Comprehensive Security Policy
An exhaustive and clearly articulated protection framework serves as the backbone of preventative security operations. This document must establish unambiguous standards for confidential information handling, system authorization protocols, and emergency response sequences. Covering elements ranging from credential administration to data obfuscation techniques, a robust policy creates a universal reference point for all stakeholders, guaranteeing alignment on security expectations and obligations.
Periodic reassessment and refinement of security guidelines remains equally critical. The dynamic nature of digital threats demands adaptable protective measures. Policy revisions guarantee continued relevance against contemporary security challenges. This iterative process reinforces organizational dedication to anticipatory protection and demonstrates proactive threat mitigation.
The Role of Artificial Intelligence in Enhancing Cybersecurity
The Growing Importance of AI in Various Industries
Machine learning technologies are revolutionizing multiple sectors including medical services, financial institutions, industrial production, and logistics networks. Pattern recognition capabilities enable streamlined operations and enhanced analytical outcomes, driving operational efficiencies and financial benefits that position intelligent automation as a catalyst for industrial advancement.
Practical implementations continue growing in complexity. Medical diagnostics now incorporate algorithmic analysis for precise condition identification and customized therapeutic regimens. Financial institutions leverage predictive modeling for transaction verification and economic forecasting. These developments underscore AI's pervasive influence across modern society.
AI's Impact on Automation and Efficiency
Intelligent automation systems are redefining business processes. Routine operational tasks handled by algorithms allow human specialists to concentrate on strategic initiatives requiring creative problem-solving. This operational streamlining translates to measurable productivity gains and improved financial performance.
Algorithmic processing minimizes inaccuracies in critical operational procedures. Precision-dependent fields like advanced manufacturing and laboratory research particularly benefit from consistent machine execution that eliminates human variability, ensuring superior output quality.
Ethical Considerations Surrounding AI Development
Advancing machine intelligence necessitates rigorous ethical examination. Critical issues including information confidentiality, algorithmic fairness, and workforce implications require deliberate evaluation and proactive policy development to ensure equitable technological benefits.
Algorithmic transparency and impartiality constitute fundamental design requirements. Development frameworks must actively prevent bias propagation while ensuring universal system accessibility. Potential exploitation scenarios demand careful risk assessment and mitigation strategies.
The Future of AI and Human Collaboration
Emerging workplace paradigms will emphasize synergistic human-machine partnerships. Cognitive augmentation through intelligent systems will enhance human performance across creative and analytical domains, driving innovation in scientific exploration and artistic expression alike.
The Need for AI Literacy and Education
Widespread technological integration makes foundational understanding essential. Developing public competency in machine learning concepts empowers individuals to engage with these transformative technologies. This includes operational principles, bias recognition, and balanced evaluation of technological implications.
Academic institutions play a pivotal role in workforce preparation. Incorporating machine intelligence fundamentals across educational programs will equip future professionals with necessary competencies, bridging human potential with technological advancement.
Building a Culture of Cybersecurity Awareness
Fostering a Proactive Approach
Establishing comprehensive security consciousness within intelligent infrastructure requires moving beyond incident response to preventive thinking. This holistic approach integrates protection principles throughout the building lifecycle—from initial design through daily operations. Security constitutes a collective responsibility spanning technical staff, maintenance personnel, occupants, and service providers. Effective culture-building demands persistent education ensuring universal understanding of risks and protective roles.
Structured awareness initiatives prove indispensable, covering social engineering tactics, credential security, and anomaly detection. Content should align with specific organizational roles, delivered through accessible formats. Continuous program refinement maintains relevance against evolving threat vectors.
Establishing Clear Policies and Procedures
Definitive operational guidelines form the framework for security-conscious operations. Documentation should clearly specify technology usage parameters, information management standards, and incident reporting workflows. These materials require regular accessibility and periodic content updates reflecting current best practices. Transparent policy communication ensures uniform compliance understanding.
Structured incident management protocols prove equally vital, guaranteeing timely reporting and resolution. Dedicated response teams with appropriate resources and training ensure effective threat neutralization. A comprehensive incident playbook represents a critical proactive security component.
Promoting a Culture of Continuous Learning
The evolving digital threat landscape necessitates ongoing education and adaptation. Regular policy reviews and training updates maintain defensive effectiveness against novel vulnerabilities. Encouraging workforce participation in threat intelligence sharing strengthens collective awareness. Periodic system evaluations and penetration tests identify emerging weaknesses for preemptive correction.
Establishing non-punitive reporting channels encourages open communication about security concerns. This psychologically safe environment fosters shared ownership of protection responsibilities, significantly enhancing organizational resilience.
Read more about Smart Buildings and Enhanced Cybersecurity Measures
Hot Recommendations
- Sustainable Real Estate Design Principles
- AI in Real Estate: Streamlining the Buying Process
- Climate Risk Disclosure: A Must for Real Estate
- Climate Risk Analytics: Essential for Real Estate Investment Funds
- Modular Sustainable Construction: Scalability and Speed
- Real Estate and Community Disaster Preparedness
- Smart Buildings and Advanced Building Analytics for Optimal Performance
- Smart Waste Sorting and Recycling in Buildings
- Sustainable Real Estate: A Strategic Advantage
- AI in Real Estate Transaction Processing: Speed and Accuracy