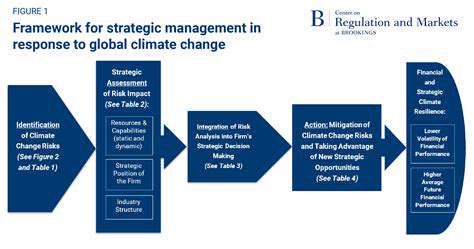
Smart Buildings: Enhancing Business Continuity and Resilience
Automated responses are revolutionizing customer service interactions, providing a more efficient and consistent experience for both customers and businesses. By leveraging technology, companies can quickly address common inquiries, freeing up human agents to focus on more complex issues. This streamlined approach ultimately leads to increased customer satisfaction and reduced operational costs.
The ability to instantly respond to customer queries across multiple channels, like email, social media, and live chat, is crucial. This immediacy fosters a sense of responsiveness and engagement, demonstrating a commitment to customer service.
Key Benefits of Implementing Automated Responses
Automated responses offer a multitude of benefits, including significant cost savings. By automating routine tasks, businesses can drastically reduce the need for human intervention, thereby lowering labor costs. This efficiency translates directly into a more profitable bottom line.
Improved response times are another key advantage. Customers appreciate quick resolutions, and automated systems can deliver answers in a fraction of the time it takes a human agent.
Types of Automated Responses
There are various types of automated responses tailored to different customer needs. Frequently Asked Questions (FAQs) are a common example, providing readily available solutions to common problems. Chatbots are another powerful tool, capable of engaging in more complex conversations and guiding customers through various processes.
Automated email responses, triggered by specific keywords or actions, can also significantly enhance the customer journey. This personalized approach ensures that customers receive the right information at the right time.
Integration with Existing Systems
A critical aspect of implementing automated responses is seamless integration with existing customer relationship management (CRM) systems. This integration allows the system to access relevant customer data, ensuring that responses are personalized and accurate.
Data-driven insights are essential for optimizing automated responses. By tracking interactions and customer feedback, companies can identify areas for improvement and refine their automated responses for better results.
Customization and Personalization
Automated responses should be adaptable to specific customer needs and preferences. The ability to personalize responses based on customer history or specific requirements is key to creating a tailored experience.
Dynamic content updates are crucial for maintaining accuracy and relevance. This ensures that the automated responses remain current and reflect the latest information available.
Training and Support for Agents
Implementing automated responses doesn't mean replacing human agents. Instead, it empowers them to focus on more complex issues and higher-value interactions. Providing proper training and support to agents on how to effectively utilize automated responses is essential for success.
By streamlining routine tasks, agents can concentrate on delivering exceptional customer service. This leads to a more engaged and satisfied workforce, which in turn benefits the customer.
Monitoring and Evaluation
Regular monitoring and evaluation of automated responses are necessary to ensure they remain effective. Tracking key metrics like response time, accuracy, and customer satisfaction is vital for identifying areas needing improvement.
Continuous refinement is crucial for optimizing the performance of automated responses. This iterative process ensures that automated responses consistently meet customer expectations and contribute to a positive brand image.
Strengthening Security Measures in Smart Environments

Implementing Robust Authentication Protocols
A critical aspect of strengthening security measures is implementing robust authentication protocols. These protocols verify the identity of users attempting to access sensitive information or systems, acting as the first line of defense against unauthorized access. Strong passwords, multi-factor authentication (MFA), and biometric verification are key elements in creating a secure authentication system. Implementing these measures can significantly reduce the risk of unauthorized access and data breaches.
Careful consideration must be given to the specific needs of the organization, including the sensitivity of the data being protected and the potential risks associated with unauthorized access. Implementing a layered approach to authentication, combining multiple methods, can further enhance security by creating additional barriers to unauthorized access.
Enhancing Data Encryption Techniques
Data encryption is an essential component of any comprehensive security strategy. It involves converting readable data into an unreadable format, making it virtually impossible for unauthorized individuals to access or understand the information. Implementing robust encryption algorithms, such as AES-256, and regularly updating these algorithms with the latest security patches are critical steps.
Encrypting data both in transit and at rest is crucial. Data in transit is encrypted during transmission over networks, while data at rest is encrypted when stored on servers or other storage devices. This dual approach ensures that sensitive information remains protected regardless of its location.
Establishing Comprehensive Access Control Policies
Establishing clear and comprehensive access control policies is vital for securing sensitive information. These policies define who has access to what data and resources, ensuring that only authorized personnel can access specific information. This helps limit potential vulnerabilities and minimize the scope of any potential data breach. Defining granular access rights for different roles and responsibilities is a key aspect of implementing these policies.
Regularly reviewing and updating access control policies is crucial for maintaining a secure environment. As organizational structures and data needs evolve, access control policies must adapt to reflect these changes. This adaptable approach ensures that the policies remain effective in protecting sensitive information.
Utilizing Advanced Intrusion Detection Systems
Integrating advanced intrusion detection systems (IDS) into the security infrastructure is a crucial step towards proactive threat detection. These systems monitor network traffic and system activities for suspicious patterns or anomalies that could indicate malicious activity. This proactive approach can help identify and mitigate potential threats before they escalate into significant security breaches.
IDS systems should be configured with specific rules and parameters tailored to the organization's unique security needs and environment. Regular updates and maintenance of the IDS system are necessary to ensure its effectiveness in detecting and responding to evolving threats.
Implementing Multi-Layered Security Measures
A multi-layered security approach is essential for protecting sensitive information and systems. Instead of relying on a single security measure, organizations should implement a combination of various security controls, such as firewalls, intrusion detection systems, and access control measures. This layered approach creates multiple security checkpoints, making it significantly harder for attackers to compromise the system. Combining multiple security protocols significantly enhances overall system security.
Regular security audits and penetration testing are crucial components of a multi-layered security strategy. These assessments help identify vulnerabilities and weaknesses in the existing security measures, allowing organizations to improve their defenses and proactively address potential threats.
Conducting Regular Security Awareness Training
Regular security awareness training for all employees is critical to maintaining a strong security posture. Educating employees about common security threats, such as phishing attacks and social engineering tactics, is essential to empower them to recognize and avoid potential risks. Empowering employees to become active participants in security is vital, as human error can be a significant vulnerability.
Regularly updating and reinforcing security awareness training programs can help maintain an environment where employees are well-equipped to handle security challenges. This ongoing education ensures that employees are up-to-date on the latest threats and best practices for maintaining security.